About the PRTG Traffic Grapher
The PRTG Traffic Grapher is a Microsoft Windows software tool for monitoring and classifying traffic bandwidth use. It offers a simple, easy-to-learn interface and provides system administrators with live readings and long-term use trends for their network devices. The PRTG Traffic Grapher is most commonly used for bandwidth management, but its sensor technology can also be used to:
• Log the amount of data flowing in and out of Simple Network Management Protocol (SNMP)-enabled network components using the Internet MIB-2 standard.
• Inspect all data packets passing a computer's network interface card (packet sniffing).
• Incorporate bandwidth use data sent by Cisco routers using the NetFlow Version 5 protocol.
The packet sniffer and NetFlow-based monitoring capabilities of the PRTG Traffic Grapher provide the capability to classify traffic by protocol, IP address, and MAC address.
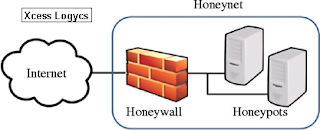
.jpg)


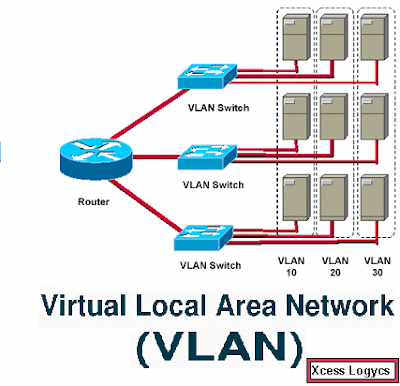










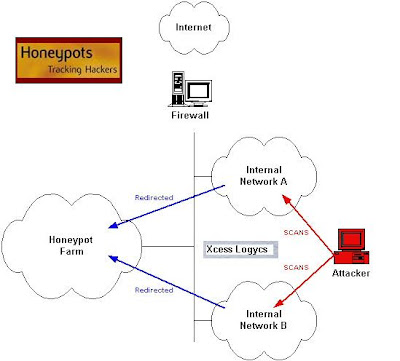





















.jpg)






