Aim: Good Articles in simple Language. {Source Of Highly Innovative Value Added Mania}
Monday 30 April 2012
Internet Download Manager v6 11 Build.5 Full (Mediafire Link)
Hi all users, today we're not going to teach how to crack IDM or how to create keygen for it, today we just want to share this cool stuff with you. For information "Internet Download Manager is a tool for increasing download speeds by up to 5 times, and for resuming, scheduling, and organizing downloads. The program will resume unfinished downloads due to network problems, or unexpected power outages. The program features a full-fledged site grabber that downloads files that are specified with filters, for example, all pictures from a Web site, different parts of Web sites, or complete Web sites for offline browsing."
How to DOX Somone ? - Find out Information of your Friend.
Hi all users today we're here with a quick and I think very simple tutorial on doxing. You’re probably thinking, “Okay, so basically it’s getting information from searching someone’s email on Google right?” in a sense yes, but there are actually easier ways to get someone’s information online, which you're going to learn on this tutorial . So lets get started.
Warning : This tutorial is for informational purposes only. I am not responsible if you use this information.
Warning : This tutorial is for informational purposes only. I am not responsible if you use this information.
How to Save All Tabs When Closing Firefox ?
Hi all users, I know this is very simple trick, but it is very worthy. Well I don't know if you noticed or not that previous versions of Firefox e.g. Firefox 3 have great option to save all tabs before closing Firefox, and it is very helpful in the case of power failure, BSOD, automatic reboot etc But Firefox 4 - 12 beta have no option to save all tabs before closing it, means this function is disabled in it's newer versions, but you need not to worry because you can enable it easily by using this simple trick :D So lets get started.
Saturday 28 April 2012
How To Run Multiple Times Of Yahoo Messenger
- (2 or more Yahoo Messenger at a Time) -
Cool Facebook Chat Images (Must Try)
Hi all users lets have fun with facebook below is some facebook chat image codes just paste it in your chat box of message box and see what will happen. But keep in mind that this only works in PC/Laptop and will not work if you're chatting from Mobile!). Don't try it in comments it will not work... try it in chat and msg from PC to your friends.
Friday 27 April 2012
Adhoc Wireless Connect:ion : Two or More Computers Together using Wireless for Sharing Internet and Files
Connect 2 laptops together to transfer some files over to another laptop but unfortunately there are no wireless router or cross link network cable. If there is a wireless router, all I need is the wireless encryption password or if I had a cross link cable, manually setting up the IP address and subnet mask will do. Luckily I could still remember the steps on how to share internet connection in Win without wireless router .
The 7 Deadly Linux Commands - Dangerous Command for Linux OS
If you are new to Linux, chances are you will meet a stupid person perhaps in a forum or chat room that can trick you into using commands that will harm your files or even your entire operating system. To avoid this dangerous scenario from happening, I have here a list of deadly Linux commands that you should avoid.
Cisco Router - Security Device Manager (SDM) v2.5

Cisco Router and Security Device Manager (SDM) is a Web-based device-management tool for Cisco routers that can improve the productivity of network managers, simplify router deployments, and help troubleshoot complex network and VPN connectivity issues.
Disable, Remove or Get Rid of Facebook Timeline Forever
Hi all users as we all know that 90% of facebook timeline users regret to have this. And this will open the door for hacker for exploiting them, means they claim to remove your timeline in few minutes but actually they are exploiting you in some extent like spamming, infecting and stealing your credentials and force you to install some app or like their pages and at last they will give you excuse saying that "I'm not responsible for that", "I have tried my level best but..." or "this is impossible to do". But now it's over today we are here to tell you a easiest, simplest and most secure way to get rid of your facebook timeline without any spamming or losing your money.
How to Bypass "ANY" Windows Login Password ?
Hi all users many of asked us "How to Bypass my Windows 7 Home Premium x64 Password", means they only want to bypass their password no to break it, and we promised them that one day we will surely come with a very easy to use tutorial so here we are, using this hack you can bypass not only "Windows 7 Home Premium x64" password but you can bypass "ANY", yes you heard right! you can bypass any windows password regardless whether they are x32 or 64x. It's really so easy so that every one can become a windows password bypasser lol. So lets get started.
How To Get Your Own Domain For Free Website ???
Hi all users, today I will tell you a website which provides a .IN domains for free with a free hosting site. It costs zero dollar yes you heard right and it doesn't ask for any credit or debit card details. I've tried this trick personally and it worked 100% for me so I thought of share this with our users.
Thursday 26 April 2012
Advanced JPEG Compressor v2012.9.3.100 Full with Crack
Reduce JPEG File Size ( 5 MB to 1.5 MB) - DIGITAL CAMERA PHOTOS
Advanced JPEG Compressor for Windows is the world's leading software for compressing digital images in JPEG format. Use Advanced JPEG Compressor for a variety of personal or business purposes: Easily reduce the large file sizes of your graphic files. Impressive file size reduction without losses in picture quality! Smaller files take less space and up and download faster. Effectively optimize photos for faster loading from the Web and faster sending by e-mail - avoid exceeding size limits. Compress scanned documents for storage/transferal.
Wednesday 25 April 2012
CISA Certified Information Systems Auditor Study Guide 3rd Edition - 2011
CISA Certified Information Systems Auditor Study Guide, 3rd Edition
David L. Cannon|ISBN: 978-0-470-61010-7|Paperback|696 pages|March 2011
More than 27,000 IT professionals take the Certified Information Systems Auditor exam each year. SC Magazine lists the CISA as the top certification for security professionals. Compliances, regulations, and best practices for IS auditing are updated twice a year, and this is the most up-to-date book available to prepare aspiring CISAs for the next exam.
David L. Cannon|ISBN: 978-0-470-61010-7|Paperback|696 pages|March 2011
More than 27,000 IT professionals take the Certified Information Systems Auditor exam each year. SC Magazine lists the CISA as the top certification for security professionals. Compliances, regulations, and best practices for IS auditing are updated twice a year, and this is the most up-to-date book available to prepare aspiring CISAs for the next exam.
JNCIE: Juniper Networks Certified Internet Expert Study Guide
JNCIE: Juniper Networks Certified Internet Expert Study Guide
Publisher: Sybex | ISBN: 0782140696 | edition 2003 | PDF | 1008 pages | 4,74 mb
Turn to this Official Study Guide from Sybex for the most extensive preparation available for Juniper Networks' highest level of certification: JNCIE (Juniper
Networks Certified Internet Expert)! At the top of a four-tiered
certification program, the JNCIE is an advanced, hands-on, lab-based
certification. Published in partnership with the Juniper Networks Technical Certification Program, and written by the lead developer of the exam, this official Study Guide
provides in-depth coverage of all exam objectives along with practical
insights drawn from real-world experience. The accompanying CD includes
the entire book in searchable PDF as well as complete router
configurations for case studies used throughout the book .
How to Create a FUD Backdoor – Bypass An Antivirus
How to bypass an Anti-virus or how to
create a FUD (fully undetectable) backdoor is not a new topic of
discussion, the need to bypass an antivirus is very high because it is
very helpful in the process of penetration testing and ethical hacking.
You can bypass an antivirus by using the metasploit encoders and there
are many other ways, in this tutorial I will show you how to make your
ncat FUD and how to use the netcat as a backdoor.
EASEUS Partition Master v9.0.0 Professional Edition (Full Software) - Mediafire link
EASEUS Partition Master v9.0.0 Professional Edition | 81 MB
EASEUS Partition Master is an all-in-one to work with partitions and drives. The program will allow you to extend a system partition, to solve problems with insufficient disk space, as well as to manage free space on the MBR and GPT disks, where the operating systems Windows 2000 / XP / Vista / Windows 7 (as x86, and x64). The program includes several tools for working with partitions: Partition Manager, Master Copy disks and partitions and partition recovery wizard. In addition, you can create a bootable CD / DVD drives in the event of a failed system boot. New! Master Partition Recovery helps to recover deleted or lost partitions Supported volume GPT - GPT disk division, copy GPT disk, restore disk, etc. Convert dynamic disks to basic disks to the preservation and protection of all available information on them Extend the system partition, to improve system performance. Partition Manager utility can help better manage the hard drive and help your computer run faster.Copy wizard to copy or move an entire partition to another hard drive without reinstalling Windows.
Google Drive Is Live With 5GB Of Free Storage And Google Docs Hookup
Google Drive Is Live With 5GB Of Free Storage with 10 GB GMAIL Space.
You can now try Google Drive, Google’s Dropbox competitor, google.com Drive.
UPDATE – The app is now available for download and I installed it, creating a folder on my computer that acts as a GDrive sync area. All of my Google Docs appeared as “icons” in the folder.
You can now try Google Drive, Google’s Dropbox competitor, google.com Drive.
UPDATE – The app is now available for download and I installed it, creating a folder on my computer that acts as a GDrive sync area. All of my Google Docs appeared as “icons” in the folder.
How to Convert Your Torrent Into Direct Link ?

Hi all users, here we're back with another essential tutorial for you.
Many of you reported us that torrific.com is no longer available (down)
and we want a good alternative for it. So today we're going to introduce
a very good alternate of torrific.com, which works with almost any
torrent. It offers two kind of services first one is free and second is
premium free one if works very well but if you're a die hard downloader
then you have to look for it's premium membership. So lets get started.
Tuesday 24 April 2012
PowerISO v4.8 + Keygen (Complete Software)
PowerISO is a powerful CD/DVD/BD image file processing tool, which allows you to open, extract, create, edit, compress, encrypt, split and convert ISO files, and mount these files with internal virtual drive. It can process almost all CD/DVD/BD image files including ISO and BIN.
Nitro PDF Professional v7.3.1.10 x86 & x64 Incl Keygen
Lastest version of Nitro PDF Professional. Nitro PDF is actually a great choice for Pdf reading and managing.
Nitro PDF Professional gives business professionals the complete, affordable and easy -to-use set of tools to work with PDF documents. Our award-winning software lets anyone easily create, combine, edit, secure, convert and collaborate with PDF files. Nitro Pro 7 gives you everything you need to create, convert, edit, sign, and share 100% industry-standard PDF files. It’s simple, straightforward, and intuitive to use — so you can work more productively, your way.
Read Your PDF Files With Nice Flipping Effect
Hi all users, as you know that PDF is the most common file format for sharing documents in the world of the Internet. Most of the e-Books too come in PDF format. To read the PDF documents Adobe PDF reader is a popular one. Most preferred Adobe PDF reader than any other light weight reader. Adobe PDF reader is lack in visual effects like flipping. If you want to put fun with you reading experience and want to use a more convenient, user friendly PDF reader you use the Flipping PDF Reader.
Monday 23 April 2012
Fast Track Hacking-Backtrack5 Tutorial
Backtrack 5 contains different tools for exploitation, as discussed before about metasploit and armitage for this article i will discuss about fast track, however I have received different request to write more tutorial for armitage, i will write for armitage too later. Fast Track is a compilation of custom developed tools that allow penetration testers the ease of advanced penetration techniques in a relatively easy manner.
Some of these tools utilize the Metasploit framework in order to successfully create payloads, exploit systems, or interface within compromised systems.
If you are beginner and dont have any idea about vulnerability, payload and shell code than first read the article " Introduction to metasploit".
Crack SSL Using SSLStrip With BackTrack5
Well this is the tutorial based article, so you must know about SSL (secure socket layer) and something about Backtrack5 because we are using backtrack5 for this tutorial, if you are using some old version like backtrack4 or if you are using some other Linux so you must be sure to install all the dependencies that being used in this tutorial.
Secure socket layer or SSL used to established a secure and encrypt connection between user and the server and we would like to break this secure connection so the sniffing will be occur successfully.
To crack SSL protection we launch man in the middle attack, so doing this we need some tools and the requirement list is
- Linux (Backtrack)
- Arpspoof
- IP Tables
- SSL Strip
- Netstat
Mantra's Browser - Hackers Best Web Browser
Mantra is a web browser made of FireFox. Its great for testing a website Vulnerabilities. My opinion it deserves a try!
Download ---> Mantra Download
Website ---> Mantra Website
Tools List
The Mantra is a powerful set of tools to make the attacker's task easier. The beta version of Mantra Security Toolkit contains following tools built onto it. You can also always suggest any tools/ scripts that you would like see in the next release.
Screen Shot
Download ---> Mantra Download
Website ---> Mantra Website
Tools List
The Mantra is a powerful set of tools to make the attacker's task easier. The beta version of Mantra Security Toolkit contains following tools built onto it. You can also always suggest any tools/ scripts that you would like see in the next release.
Sunday 22 April 2012
CCSE NG: Check Point Certified Security Expert Study Guide
Description
CCSE NG: Checkpoint Certified Security Expert Study Guide
Publisher: Sybex | ISBN: 0782141161 | edition 2003 | PDF | 656 pages | 9,44 mb
Publisher: Sybex | ISBN: 0782141161 | edition 2003 | PDF | 656 pages | 9,44 mb
Labels:
E-Book,
Firewall,
IT Security,
Windows Softwares
Saturday 21 April 2012
CCSA NG: Check Point Certified Security Administrator Study Guide
Description
CCSA NG: CheckPoint Certified Security Administrator Study Guide
Justin Menga | Sybex | 2011-01-25 | 656 pages | English | PDF
Author: Justin Menga
Date: 2011-01-25
Pages: 656
Publisher: Sybex
Category: Technical
Here's the book you need to prepare for Check Point's VPN-1/FireWall-1 Management I NG exam, #156-210. Written by a Check Point security expert who knows exactly what it takes to pass the test
Labels:
E-Book,
Firewall,
IT Security,
Windows Softwares
Thursday 19 April 2012
Metasploit Tutorial 2
Basics Part 2 - Using The Inbuilt Codes
Welcome to the Metasploit Basics Part 2 . Make sure you read the first part before reading this.In this part we will talk about using the Exploits , Payloads , Auxiliary , Nops and Encoders.I think i don't need to explain what are these because it is already discussed in the first part
Metasploit have
+ -- --=[ 684 exploits - 355 auxiliary
+ -- --=[ 217 payloads - 27 encoders - 8 nops
This may vary in your metasploit according to your version.
The Basic use of metasploit
1. Pick which exploit to use
2. Configure the exploit with remote IP address and remote port number
3. Pick a payload
4. Configure the payload with local IP address and local port number
5. Execute the exploit
Now time for a example
Type "show exploits" see the list of exploits available. Many of the exploits listed here are going to work against the target servers.But the difficult part is to know if the exploits will work or not =P
I will use ....
Welcome to the Metasploit Basics Part 2 . Make sure you read the first part before reading this.In this part we will talk about using the Exploits , Payloads , Auxiliary , Nops and Encoders.I think i don't need to explain what are these because it is already discussed in the first part
Metasploit have
+ -- --=[ 684 exploits - 355 auxiliary
+ -- --=[ 217 payloads - 27 encoders - 8 nops
This may vary in your metasploit according to your version.
The Basic use of metasploit
1. Pick which exploit to use
2. Configure the exploit with remote IP address and remote port number
3. Pick a payload
4. Configure the payload with local IP address and local port number
5. Execute the exploit
Now time for a example
Type "show exploits" see the list of exploits available. Many of the exploits listed here are going to work against the target servers.But the difficult part is to know if the exploits will work or not =P
I will use ....
Google Images Search Under Water !!!
Hi all users,
Here is another great Google search bar which is Google
Images Search Under Water as you see in below image. Recently I found
this amazing page, where I notice that the Google logo is floating under
the water with shark and fishes. It is looks like same as Google
Gravity. In their search engine you can search any images and it will
show the results than the image will goes on under water. The more you
click on search link the more images will fall.
Difference Between IRC botNet and A Booter
What is A Bot?
A Bot is a program that runs on a computer
and giving information to the creator. Bots can be created by using a
language such as C++ or vb..Today these languages are the common
languages used to create Bots. After compiling a Bot we get a .exe file
witch we call the Bot or it is the file we send to a slave.
What does A bot do?
Basically when a bot runs in a computer it
can collect valuable information from the slave pc such as cd keys ,
passwords etc .And it can send these data to the creator of the bot.
What is a BotNet?
Bot creator make their bots to connect to a
command control center, So the Bot creator can command their bots or
can get data from bots through it .Basically we now use IRC , Booter or
PHP (web Based) controls.
What is a Booter and a IRC BotNet?
How to Upload Your File to multiple Hosts ?
uploads your file to several free hosting providers. You just need to upload your file to our server once, it will be automatically uploaded to several free file hosts like RapidShare, MegaUpload. After the file is uploaded to our server, you will get the link to the download page which contains the all the download links.
How do I upload a file?
Go and click the Browse button near the middle of the page. A file dialog box will appear on your screen. Select a file you want to upload. Then click the Upload button and wait for your file to finish uploading. That's it, the rest is done by us.
Where is the Download Link?
Send emails from someone else's account without knowing their password!

Hi all users, today we're going to show you another cool site where you
can send fake e-mails means by using this site you can send e-mails from
anyone's e-mail (e-mails spoofing) . So this this what it's author said
about it.
"I know you know another site which can send fake e-mails but I have
just finished setting up an email server on my website and I just need
to show it off :).
That's why I made a small page from which you can send mail, that looks like it came from someone else.
Wednesday 18 April 2012
The Official CHFI Study Guide (Exam 312-49)
The Official CHFI Study Guide (Exam 312-49) | 11.8 MB
This is the only official, EC-Council-endorsed CHFI (Computer Hacking Forensics Investigator) study guide.
It was written for security professionals, systems administrators, IT
consultants, legal professionals, IT managers, police and law
enforcement personnel studying for the CHFI certification, and
professionals needing the skills to identify an intruder’s footprints
and properly gather the necessary evidence to prosecute. Key features
include:
The Only Official Study Guide for CHFI
- Provides 100% coverage of all exam objectives.
- Full Web-based Exam
- Modeled after the real exam, it also includes explanations of correct and incorrect answers.
- Exam Objectives
- Each is clearly explained at the beginning of the chapter.
- Notes and Alerts
- Highlight crucial points of the exam modules.
- Exam Objectives Fast Track
- Bulleted highlights emphasize the important points from the exam’s perspective at the end of the chapter.
Hacking Exposed: Web Applications, 3rd Edition
Book Description
The latest Web app attacks and countermeasures from world-renowned practitioners
Protect your Web applications from
malicious attacks by mastering the weapons and thought processes of
today’s hacker. Written by recognized security practitioners and thought
leaders, Hacking Exposed Web Applications, Third Edition is fully updated to cover new infiltration methods
and countermeasures. Find out how to reinforce authentication and
authorization, plug holes in Firefox and IE, reinforce against injection
attacks, and secure Web 2.0 features. Integrating security into the Web development lifecycle (SDL) and into the broader enterprise information security program is also covered in this comprehensive resource.
Career Academy – Certified Ethical Hacker v7 (CEH) 3 DVDs
Career Academy – Certified Ethical Hacker v7 (CEH) 3 DVDs
English | 3 DVDs | ISO | 5.36 GB
Genre: Video Training
English | 3 DVDs | ISO | 5.36 GB
Genre: Video Training
EC-Council CEH Certified Ethical Hacker v7.1 Training – OnDemand Learning
This class will immerse the student into an interactive environment where they will be shown how to scan, test, hack and secure their own systems. The lab intensive environment gives each student in-depth knowledge and practical experience with the current essential security systems.
Students will begin by understanding how perimeter defenses work and
then be lead into scanning and attacking their own networks, no real
network is harmed. Students then learn how intruders escalate privileges
and what steps can be taken to secure a system. Students will also
learn about Intrusion Detection, Policy Creation, Social Engineering,
DDoS Attacks, Buffer Overflows and Virus Creation. When a student
completes the course they will have hands on understanding and
experience in Ethical Hacking. This course prepares you for EC-Council
Certified Ethical Hacker exam 312-50
What is Denial of Service Attack (Dos Attack)
Hello everyone, by reading our previous post you might know that what is Ddos attack and how does it work?
, so today I want to share you a detailed tutoriallon denial of service
attack and it's technique so lets get started Denial of Service or
(DoS) or sometime referred as Distributed Denial of Service (DDos)
attacks have matured from mere annoyances to severe high-profile attacks
to e-commerce sites. When performing DoS attacks there are alot of
approached techniques, including the famous but old "Ping of Death"
which will be covered in this tutorial. DoS has been raging on since the
90's, getting more advanced and more serious. This tutorial is going to
explain the jist of it to you.
Free Windows 8 Download - Direct Link
Hi all users, here we've collected together some Official + Mirror
Direct Links to Download Windows 8 DVD .ISO 32-bit & 64-bit
Installation Image (Dev Preview Edition) – After getting some leaked
editions previously, finally an official Developer Preview edition has
been made available for download.
As the next generation to continue the success of Windows 7, Microsoft
Windows 8 system requirements are quite similar to Windows 7. It means,
as long as your PC can run Windows 7 smoothly, then you should be able
to install Windows 8 on your current specs. Some minimum specs for
Windows 8 are: 1GHz Processor with 1 GB of RAM, 16 GB of free hard drive
space and a DirectX 9 graphics card with WDDM 1.0 or higher driver.
Metasploit Tutorial 1 - Understanding The Framework
What is Metasploit ?
The Metasploit Project is an open-source computer security project which provides information
about security vulnerabilities and aids in penetration
testing and IDS signature development. Its most well-known
sub-project is the Metasploit
Framework, a tool for developing and executing exploit code against a remote
target machine. Other important sub-projects include the Opcode Database,
shellcode archive, and security research.
Basically
Metasploit is tool which provides complete environment for hacking.
Metasploit is ran by rapid7 community &
Metasploit is the biggest software which is written in ruby
Why metasploit is recommended ?
1. metasploit is free n easy to use and one can develop
his own exploits,payloads etc & use it with metasploit easily.
2. It comes with over 690 exploits & which
are updated on regular basis(0days also included).
3. We can use diffrent plugins,external tools to
improve the productivity of metasploit for example SET(social engineering
toolkit), beEF, XSSF, Nexpose , NMAP, W3af etc(we will continue to it in next
posts)
Metasploit
is available in 3 versions
1. Metasploit Pro - for pentester
2. Metasploit Express- for IT security teams
3. Metasploit Framework - Its an open source & avialable for download
for free
you can download metasploit from official website - www.metasploit.com
Labels:
Exploits Articles,
IT Security,
Windows Softwares
Ethical Hacking - An Overview of Ethical Hackers
Ethical Hacking - An Overview of Ethical Hackers
Hi
all users, today we're glad to present you the another detailed and
well written article on ethical hacking and we're sure that this will
definitely help you to know "what the exactly ethical hacking is?" and
all about ethical hacking for the person interested and curious to know
more about ethical hacking. So lets read on.
How to Reset Windows Password Using BackTrack
How to Reset Windows Password Using BackTrack
Hello all users, in today's we'd like to share a very simple and eagyhack for resetting
your the lost Windows password using BackTrack & Chntpw tool, so
let me get straight to the point without beating around the bush.
Windows stores the login password hashes (lm/ntlm format) in the registry hive files named 'SYSTEM' and 'SAM' at following location
Friday 13 April 2012
METASPLOIT FRAMEWORK
Metasploit Framework is command line framework of metasploit where everything is to be done manually with commands it is much stable than other GUI versions of metasploit.
Metasploit Framework is free to download as we all know metasploit is open source.
Labels:
Exploits Articles,
IT Security,
Windows Softwares
Thursday 12 April 2012
Install Windows 7 with USB flash drive
Almost no computer skills is required for this method.
1. Obtain a Windows 7 ISO file (This will be recieved when buying Windows 7 from Microsoft's website, or by using your current Windows 7 DVD. You'll need PowerISO (http://www.poweriso.com/) to make the DVD into a .iso file.)
2. Download and install Windows 7 USB/DVD download tool (link) You may follow a short guide here
WHAT IS METASPLOIT
The Metasploit Project is an open-source computer security project which provides information about security vulnerabilities and aids in penetration testing and IDS signature development. Its most well-known sub-project is the Metasploit Framework, a tool for developing and executing exploit code against a remote target machine. Other important sub-projects include the Opcode Database, shellcode archive, and security research.
Labels:
Exploits Articles,
IT Security,
Windows Softwares
Metasploit – The Penetration Tester’s Guide Ebook
"The best guide to the Metasploit Framework." —HD Moore, Founder of the Metasploit Project
The
Metasploit Framework makes discovering, exploiting, and sharing
vulnerabilities quick and relatively painless. But while Metasploit is
used by security professionals everywhere, the tool can be hard to grasp
for first-time users. Metasploit: The Penetration Tester's Guide
fills this gap by teaching you how to harness the Framework and
interact with the vibrant community of Metasploit contributors.
Once you've built your foundation for penetration testing, you'll learn the Framework's conventions, interfaces, and module system as you launch simulated attacks. You'll move on to advanced penetration testing techniques, including network reconnaissance and enumeration, client-side attacks, wireless attacks, and targeted social-engineering attacks.
Learn how to:


- Find and exploit unmaintained, misconfigured, and unpatched systems
- Perform reconnaissance and find valuable information about your target
- Bypass anti-virus technologies and circumvent security controls
- Integrate Nmap, NeXpose, and Nessus with Metasploit to automate discovery
- Use the Meterpreter shell to launch further attacks from inside the network
- Harness standalone Metasploit utilities, third-party tools, and plug-ins
- Learn how to write your own Meterpreter post exploitation modules and scripts
Labels:
E-Book,
Exploits Articles,
Hacking Articles,
IT Security
Download CentOS 6.1 CD / DVD ISO
CentOS Linux version 6.1 has been released
and available for the download. It is a community-supported operating
system based on Red Hat Enterprise Linux (RHEL) version 6.1. CentOS
Linux is considered as the most popular Linux distribution for web
servers and general purposes usage.
From the release note:
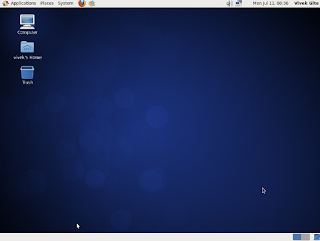
CentOS Linux 6.x Desktop Screenshot
From the release note:
CentOS-6.1 is based on the upstream release EL 6.1 and includes packages from all variants. All upstream repositories have been combined into one, to make it easier for end users to work with. CentOS conforms fully with the upstream vendor's redistribution policy and aims to be 100% binary compatible. (CentOS mainly changes packages to remove upstream vendor branding and artwork.)
Google Public DNS – Use and Boost your DNS Caching Speed
Have you ever tried to change nameservers of your website? What happens then?
Your domain registrar changes them into your new nameservers and then they update their records of your nameservers. And let those new nameservers to be public. And when your ISP(Internet Service Provider) accesses the registrar’s database, they find the modification to your nameservers and update their records as well. So then you can access your website which is on different nameservers now.
This looks like a 1-2-3 process. But it is not.
UltraSurf v8.8 0 - Bypass All Internet Blocking Systems
UltraSurf is a proxy application. It will Bypass All Internet Blocking
Systems. By using this software you can access all the sites blocked by
national / corporate firewalls. It is a free application. It brake all
the access list. This application is nothing but just searching the proxy list which
is fast and available. It will automatically change our IE’s proxy
server to local proxy. That means this application will work as a web
proxy server. Most of the schools and co-operates are blocking dating
sites like orkut , myspace. And some sites like YouTube ( for bandwidth
). Most of them depending web proxys to bypass them. But they won’t get the full feeling of a normal browsing , because the sites are with banners.
User Friendly Nmap with Zenmap GUI
Nmap is a very popular and powerful security scanner that can be used to discover hosts and services which has been in development for more than 10 years. It is unlike any simple port scanner where you enter an IP address and it will sweep through 65535 ports to look for any open ports and inform you the common service that is normally running on that open port. Nmap is able to accurately detect the service and version even if the service is running on some obscure port. Another well known feature of Nmap is the ability to tell what operating system is on the machine. It also support scripting allowing users to write (and share) simple scripts (using the Lua programming language, ) to automate a wide variety of networking tasks. One example is a built-in script that is able to detect whether a host is infected with the Stuxnet worm.The current version of Nmap 5.51 contains a total of 178 scripts.
Subscribe to:
Posts (Atom)
















.jpg)















.png)



.png)