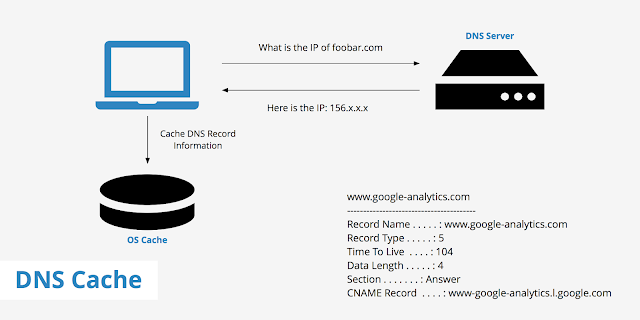
What Is chrome://net-internals/#dns?
You can try this link on your browser and you will see the page where you can click Clear host cache to clear the DNS cache on Chrome.
The net-internals/#dns, also known as Net-Internals, is a NetLog event stream visualisation tool where you can view real-time logs or load NetLog dumps of later dates that keep the browser’s network-related events and state, helping troubleshoot and debug problems.
Is It Necessary to Clear DNS Cache on Chrome?
There are some situations when you need to perform chrome://net-internals/#dns.
- When you are unable to access a website and the DNS entry has been changed.
- When you changed the DNS servers of your network adapter and apply that setting.
- When some errors repeatedly occur to tell you some commonly used websites are un-trusted.
How to Clear DNS Cache?
1. Clear DNS Cache on Chrome
Step 1: Open your Chrome browser and go to this link: chrome://net-internals/#dns.
Step 2: Once you get to this page, you will see the page with the Clear host cache button and click on the button.
After this move, no message or prompt will show you the result but you have flushed the DNS cache on Google Chrome.
Step 3: Restart your Chrome browser and go to this link: chrome://net-internals/#sockets.
Step 4: Hit the Flush socket pools button and then restart your browser.
2. Clear DNS Cache on Firefox
You can clear DNS cache on Firefox by simply restarting the browser for the cache is not maintained on the disk. Or if you don’t want to restart your browser, you can do as follows.
Step 1: Open your Firefox browser and enter this link in the address bar: about:networking#dns.
Step 2: On the next page, you can see some DNS cache details and choose the Clear DNS Cache button to clear the browser’s DNS cache.
3. Clear DNS Cache on Safari
There is no direct button available for clearing the DNS cache on Safari but you can choose a hidden button to clear caches that include DNS caches.
Step 1: Launch Safari on your device and in the menu bar, choose Safari and then Preferences….
Step 2: In the Preferences pane, go to the Advanced tab and check the box next to Show Develop menu in menu bar.
Step 3: Then the Develop menu will appear in Safari’s menu bar and you need to click on it to choose the option of Empty Caches from the drop-down menu.
Then you can re-launch Safari and your cache will be cleared.
4. Clear DNS Cache on Opera
To clear the DNS cache on Opera, you can do as follows.
Step 1: Launch Opera on your device and go to the link: opera://net-internals/#dns.
Step 2: On the next page, you can click the button labeled Clear host cache to flush the DNS cache.
Step 3: After that, go to the link: opera://net-internals/#sockets and click on the Flush socket pools button.
5. Clear DNS Cache on Your Apple iPhone
To clear your iPhone DNS cache, you can directly restart the device, that will help clear out your DNS, or you can toggle Air-plane mode on and off.
Besides, you can reset network settings to clear DNS, but this method will clear your saved Wi-Fi and Bluetooth settings, which needs to be reconfigured.
Step 1: In Settings on your device, choose General.
Step 2: Scroll down to choose Transfer or Reset iPhone and then tap on Reset.
Step 3: Choose Reset Network Settings from the list and then confirm your option to save the choice.
After that, if you had previously customised your DNS servers, you must manually reset them again.
6. Clear DNS Cache for Your Android
Android doesn't offer a direct way to clear the system's DNS cache within the UI, but you can flush the DNS cache using a browser as we have introduced above, like Chrome, Firefox, Opera, and Safari.
Just open your mobile phone and open the browser your are using to follow the above steps to clear the DNS cache. That will be easy to follow.
